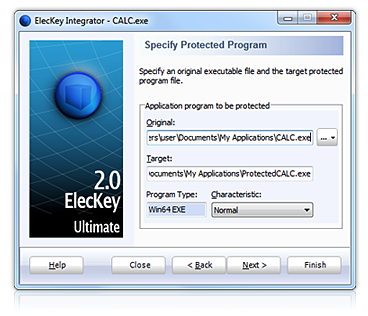
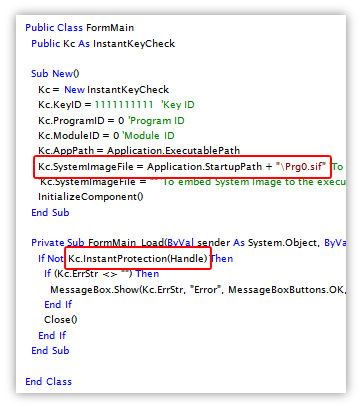
The
KeyCheck API offers an alternative to the shell protection, which allows you to integrate the software protection and licensing functionality right into your application. The API includes 32/64-bit DLLs, ActiveX, .NET Class Library, and .NET Component, with lots of example projects for study and code reuse. For macOS applications, the
KeyCheck SDK for Mac is provided, including the library and example projects for XCode, Objective-C, C++.
Greater Flexibility
Support more types of applications including .NET WPF, non-standard executables (e.g. Visual FoxPro, MS Access/Excel/Word Macro), and more.
Better Seamless Integration
Make any customization you want. For instance, seamlessly add the license registration and activation menu within your application.
Enhanced Security
Customize or add more security measures. For instance, create random key-value challenges/responses to the Key to protect against DLL emulation and dongle emulation.